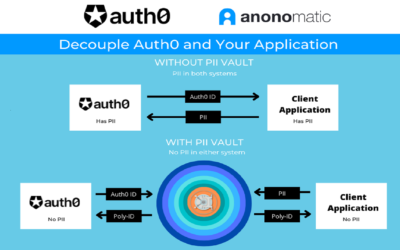
As a $122B company, AT&T spends more on data security and protection than most organizations. Without any direct knowledge of their specific security measures, except that they follow ISO/IEC 27001 standards, it is safe to assume they have firewalls, access...