The Anonomatic Blog
Thoughts and tips to help you solve Personally Identifiable Information (PII) compliance
Subscribe to get the latest content in your inbox
PII Compliance
PII-as-a-Service™
Inside Anonomatic
Subscribtion
Most Recent Post
Data Security with Optionality
RSA on Life Support, You Still Have Time to Protect Your Data
The hottest data security discussion topic last week was the claim that RSA encryption had been effectively hacked. While RSA isn’t dead yet, it is effectively on life support because few doubt that the time is quickly coming when this will be our new reality. So how...
Post Quantum Resistance with Multi-dimensional Result Factoring
Chances are, you’ve never heard of Multi-dimensional Result Factoring (MRF). That’s because it’s brand-new technology in data protection. Until it was invented by Anonomatic, every form of data protection —including all legacy technologies such as encryption—was...
Customer Success Story
Anonomatic was invited to present a customer success story at Teradata Possible 2024. Anonomatic worked with Teradata and the customer, C&A Mexico to install, validate and operationalize the solution in just two weeks! See the entire presentation here
Customer Success Story Presented at Teradata Possible
Teradata is the undisputed leader in enterprise data warehouses. Their 2024 annual user conference for US-based customers is in Los Angeles the week of October 7th. Anonomatic is thrilled to be able to present a joint customer success story during this conference....
NSF Privacy-Preserving Data Sharing & Analytics (PPDSA) Funding Opportunity
The National Science Foundation (NSF) released a solicitation for Privacy-Preserving Data Sharing in Practice (PDaSP) Privacy-Preserving Data Sharing in Practice (PDaSP) | NSF - National Science Foundation. In summary this proposal: “Supports the advancement of...
Creating trusted data with Teradata VantageCloud and Anonomatic
Anonomatic is thrilled to have provided so much value to C&A Mexico and our partner Teradata. See the full customer success story. Creating trusted data with Teradata VantageCloud and Anonomatic | Teradata
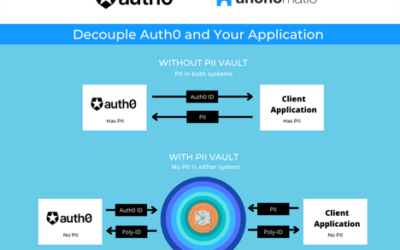
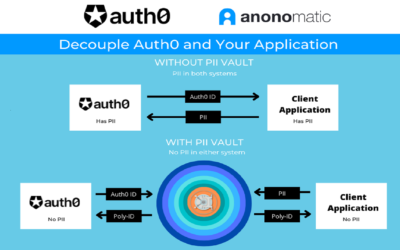
Make Your App GDPR Compliant with Auth0 & Anonomatic
Do you want to be GDPR compliant with one simple step? Seem too good to be true? Seem too easy? It’s possible! If you’re going to reduce your costs and time to market by using an Identity-as-a-Service solution like Auth0, why not get to market even faster, save even...
Meet the Tiny Non-Profit Whose Data is More Secure Than AT&T’s (and Yours)
As a $122B company, AT&T spends more on data security and protection than most organizations. Without any direct knowledge of their specific security measures, except that they follow ISO/IEC 27001 standards, it is safe to assume they have firewalls, access...
Training Your AI with Identified Data Safely
AI is not only the easiest new trend to spell, it is also making the biggest promises and getting the most investment of any new tech, ever. So, what is keeping it back? The answer is also easy to spell, PII. The reality is that even with all the potential, all...
Answering Unanswerable Questions
“No, you can’t have that data!” This is what far too many people get as an answer when they ask for access to sensitive data. But imagine if you were told you had to get huge amounts of highly sensitive, strictly regulated data and it was your job to keep it safe...
“Degenerate AI” Hackers Are Coming
“The best laid schemes of mice and men often go awry” Robert Burns Generative AI is going to be a major disruption to many industries. From teaching children how to write, to training would-be software developers how to code, there is a lot of discussion about how...
Keeping Data Private from I.T.
Your tech staff doesn't need to see production data - really, they don't. Implementing effective data privacy may seem like a daunting task. Constantly evolving national and international regulations like GDPR and CPRA make keeping up with the rules a heavy burden. At...
Data Extortion is Real. So is the Protection.
Hackers have moved from Ransomware to Data Extortion. The good news is you can ignore them. Congratulations. You hardened your systems against ransomware. Now, if you are hit, you can restore your systems and don’t have to pay. Well done. However, hackers have morphed...
Data Privacy Experts are Asking the Wrong Question
The core concern of Data Privacy is protecting the privacy of individuals. In the world of electronic data, this always meant enacting manual processes and technical solutions with the intent of limiting who can access data, when that data is allowed to be accessed,...
Q&A with Anna Azaloff, MBA, SHRM-CP, Healthcare Data Analyst for Oncology Practice Solutions
PII Vault is changing the way people manage and protect data. It is also enabling people to spend more time discovering insights within their data and less time on legacy workflows. We thought others would be interested to learn just how much more productive people...
Anonomatic PII Vault Now Available on Auth0 Marketplace
Eliminate the need to store any PII in Auth0, helping customers meet their data privacy compliance needs. We are pleased to announce the availability of PII Vault™ on Auth0 Marketplace, a catalog of trusted technology integrations to extend the functionality of...
Hackers Want Your Encrypted Data
An interesting trend is taking place in the world of data hacking. Hackers are greedily collecting untold volumes of encrypted data knowing they cannot use it today. While this may seem confusing, it is no surprise to many data security professionals, and it can only...
Anonomatic Could Save the U.S. Economy $100B+ a Year!
Federal data privacy laws have been slowly moving through congress for years and there has been real progress made recently, with a bi-lateral agreement called the American Data Privacy and Protection. But not everyone has been waiting for the law to be passed before...
Advisor Spotlight: Dr. Troy Mounts, MD, MA, FAAOS, Chief Medical Advisor
Picking up from where we left off with advisory board member profiles late last year, we’ll continue our spotlight series with Dr. Troy Mounts, MD MA FAAOS and Anonomatic’s Chief Medical Advisor. Dr. Mounts is an orthopedic spine surgeon whose passion for helping...
Walking the Fine Line between Data Privacy and Digital Transformation
A few thoughts as I prepare to meet and network with fellow privacy professionals and others committed to privacy and data protection at the IAPP Global Privacy Summit in Washington DC. Digital Transformation is a Challenge to Privacy Professionals ...
Data Mesh and Data Privacy – You CAN Have Both
When I was first introduced to the idea of data meshes, I thought it was one of those incredibly brilliant ideas which simply took someone clever enough to look at a common problem from an uncommon perspective. According to Starburst.io, data mesh is a new approach...
Use Data as Safely and Anonymously as Listening to Over-the-Air Radio
Data scientists know more than anyone else that good quality data is the foundation for useful artificial intelligence (AI) and machine learning (ML) models. Only when data quality is good, usable and from multiple sources is when the real potential of AI and ML can...
Dumb Anonymous Data vs. Smart Anonymous Data.
We’ve Seen Differences Like This Before Chances are you have never heard the term ‘dumb anonymous data’. I know I hadn’t the first time I said it. For me the term clicked immediately. It was just one of those descriptions that once...
Moving data with PII to the cloud? Watch out for rocks!
I don’t know how many different pictures and icons I’ve seen to illustrate cloud services, but they always represent a soft, cushy and very safe environment. Ask any PII data privacy specialist, and they will likely give you very different points of view. That has not...
Advisor Spotlight: Greg Neal Akers, Former SVP & CTO of Advanced Security Research & Government at Cisco
Next on our list of Anonomatic advisors we’re highlighting is Greg Neal Akers, former SVP and CTO of Advanced Security Research & Government at Cisco and currently a leading consultant to government affiliated organizations, startups, and large enterprises with...
Anonomatic Advisor Spotlight: Ron Ricci, Founder & CEO, The Transparency Imperative
Anonomatic has an excellent roster of advisors, so we wanted to start a series highlighting this A-team. For our first one, we welcome Ron Ricci, founder and CEO of The Transparency Imperative, an organization making it possible to measure the transparency of...
Make life easier by realizing data privacy is a software problem
At Anonomatic we talk to a lot of people who have a myriad of issues surrounding Data Privacy. An interesting trend we’ve noticed is the older, more established the organization, the more likely they are to consider Data Privacy to be a legal matter best addressed...
The incredible cost of implementing data privacy… or not
How long is it going to take and how much is it going to cost? Every CxO in response to every proposal ever. I think I learned my most important lesson in business back when I was in high school, and as is normal at that age, did not realize it for years to...
Data Driven Decisions vs. The Law of Diminishing Returns
Quote of the day “Your goal shouldn't be to buy players. Your goal should be to buy wins. In order buy wins, you need to buy runs.”Peter Brand: Moneyball I’m not saying it was like my first kiss, or my first major league game, but I clearly remember when I first...